One year ago, Gartner named Post-Quantum Cryptography (PQC) a top strategic technology trend for 2025 and urged organizations to start transitioning to PQC without further delay, citing lack of vendor preparedness and lack of organizational knowledge in dealing with PQC as the key obstacles on the way to timely PQC migration.
Gartner analysts emphasized that the so-called “Harvest Now, Decrypt Later” attacks are already here. Harvest Now, Decrypt Later attack is a comparatively novel cyber threat, when cybercriminals collect highly sensitive encrypted data – that currently cannot be decrypted using modern-day technologies – to stealthily wait until quantum computing becomes widely available and capable of breaking the encryption.
Earlier this year, Forrester backed Gartner’s concerns over PQC unreadiness and serious risks, estimating that current encryption will become vulnerable and breakable in 10 years from now, while emphasizing that this could happen much faster. Cloudflare, on its side, released a report saying that in 2025 as little as 38% of TLS traffic under its management was supporting some form of post-quantum (or quantum-resilient) encryption, however, stating that in some European countries the situation was comparatively better.
In response to the looming PQC threat, many governments have released guidelines and frameworks on PQC implementation including the European Commission, the UK National Cyber Security Center and the US Department of Homeland Security.
To help organization with their PQC journey, the SSL/TLS Security Test by ImmuniWeb now verifies – in addition to the full spectrum of other cryptographic and security checks – whether an TLS stack is compliant with the Federal Information Processing Standard (FIPS) 203 (“Module-Lattice-Based Key-Encapsulation Mechanism Standard”) from the most recent Post-Quantum Encryption Standards released by NIST:
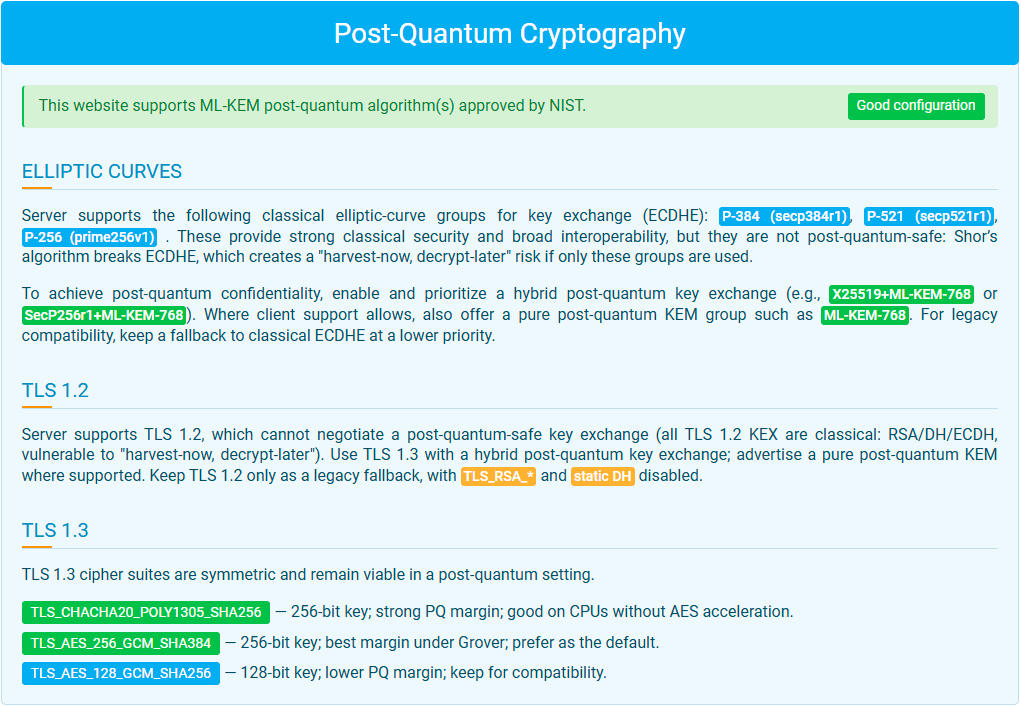
TLS Security Test: Post-Quantum Encryption Standards Verification Tab
The free online test also checks whether an TLS configuration is in conformity with technical requirements of PCI DSS, HIPAA and other NIST guidelines on cryptography.
Dr. Ilia Kolochenko, Chief Architect & CEO at ImmuniWeb, says: “Many large organizations around the globe still seriously underestimate the risks of quantum attacks.
First, with Harvest Now, Decrypt Later attacks – already being deployed by both organized cybercrime and nation-state hackers – your data may be already at risk of a guaranteed compromise in the foreseeable future. Second, although powerful quantum computers will quite unlikely become readily available to cyber-threat actors upon their creation, many vendors and organizations are totally unprepared for a rapid migration to post-quantum cryptography. Worse, some devices and business-critical systems simply do not support PQC and shall be physically replaced.
According to the ImmuniWeb’s statistics, based on over 100,000,000 tested TLS servers, millions of servers around the globe still rely on the SSLv3 protocol, which has been deprecated for over a decade. This is a telling illustration that PQC migration will likely take even longer, therefore, it is dispositive to commence your PQC migration planning and implementation now.
Today, we are delighted to offer a simple and efficient solution to organizations of all sizes to reliably verify their PQC preparedness with our online SSL/TLS testing tool. It can be easily accessed either with a user-friendly web interface or via an API for DevSecOps and CI/CD automation. More exciting news and announcements are coming soon, please stay tuned.”
Test if your servers have a quantum-resilient TLS stack here.

