Novel anti-bot services are being advertised on the dark web, offering cybercriminals advanced tools to bypass Google’s protective ‘Red Page’ warnings in a concerning development for cybersecurity teams. These services represent the latest evolution in the ongoing cat-and-mouse game between cybercriminals and security measures. To learn more about combating phishing attackers using anti-bot services, check out our SlashNext Complete page.
Phishing, a long-standing tactic in cybercrime, has become increasingly sophisticated with the rise of phishing-as-a-service (PhaaS) platforms. These platforms have democratized cybercrime, allowing even novice criminals to launch large-scale phishing campaigns with minimal technical knowledge. However, a persistent challenge for these cybercriminals has been avoiding detection by cybersecurity services like URLScan, which scan and block malicious websites.
Google’s Safe Browsing ‘Red Page‘ warning has been a particularly effective deterrent, alerting users to potential dangers and significantly reducing the success rate of phishing attacks. Now, these new anti-bot services threaten to undermine this line of defense, potentially exposing more users to sophisticated phishing attempts.
The “Google Red Page”
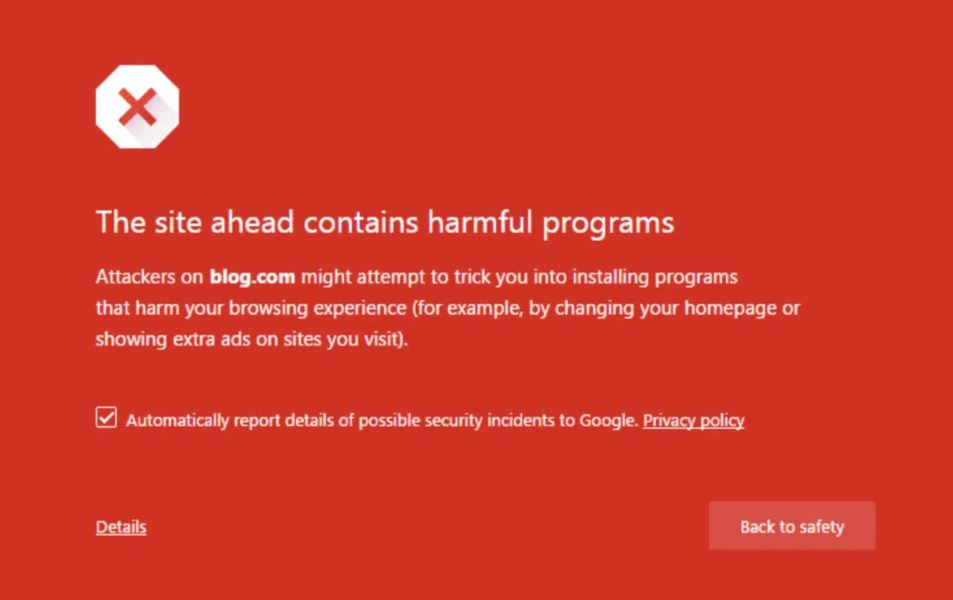
Google Safe Browsing’s “Red Page” is a security feature that protects users from harmful websites by warning them of potential dangers, such as phishing attempts. This red warning page advises users to avoid the site, severely limiting the potential success of phishing attacks.
An example of what the Google “Red Page” looks like
For cybercriminals, Google’s detection systems present a massive hurdle. Phishing campaigns rely on high click-through rates, but once Google or other security platforms flag a page, the campaign’s effectiveness plummets. Therefore, to stay ahead, criminals have developed “anti-bot” or “anti-red page” services to circumvent detection.
The Rise of Anti-Bot Services
Anti-bot services, like Otus Anti-Bot, Remove Red, and Limitless Anti-Bot, have become a cornerstone of complex phishing operations. These services aim to prevent security crawlers from identifying phishing pages and blocklisting them.
By filtering out cybersecurity bots and disguising phishing pages from scanners, these tools extend the lifespan of malicious sites, helping criminals evade detection longer.
Otus Anti-Bot
Otus Anti-Bot is one of the most popular solutions, claiming to deploy behavioral analysis, challenge-response mechanisms, bot signature detection, and integration with threat intelligence feeds. What sets Otus apart is its incredibly quick deployment—users can get it running on their phishing pages in under two minutes.
The cybercrime forum thread design for Otus Anti-Bot
Once deployed, Otus allows dynamic configuration changes, meaning the user only needs to paste the code once, and any updates to protection settings are applied in real time across multiple pages. The platform also offers easy IP and country-based whitelisting for customized testing and targeting.
Remove Red
Remove Red focuses on proactive removal of red page warnings rather than prevention alone. They claim to offer a temporary whitelist feature, which keeps the domain safe from reappearing on Google’s red page for a few days after the initial removal.
The cybercrime forum thread design for Remove Red
In addition to this, Remove Red provides monitoring services, keeping an eye on domains and notifying users via Telegram or Discord if their phishing sites are flagged again. This combination of removal and monitoring allows phishers to keep their sites online longer without constantly worrying about red page blocks.
Limitless Anti-Bot
Limitless Anti-Bot claims to extend the lifespan of phishing sites by adding a small piece of code to the page. The service emphasizes prevention over reactive removal, using advanced tools, AI, ISP information, and user-agent identification to distinguish between real users and bots.
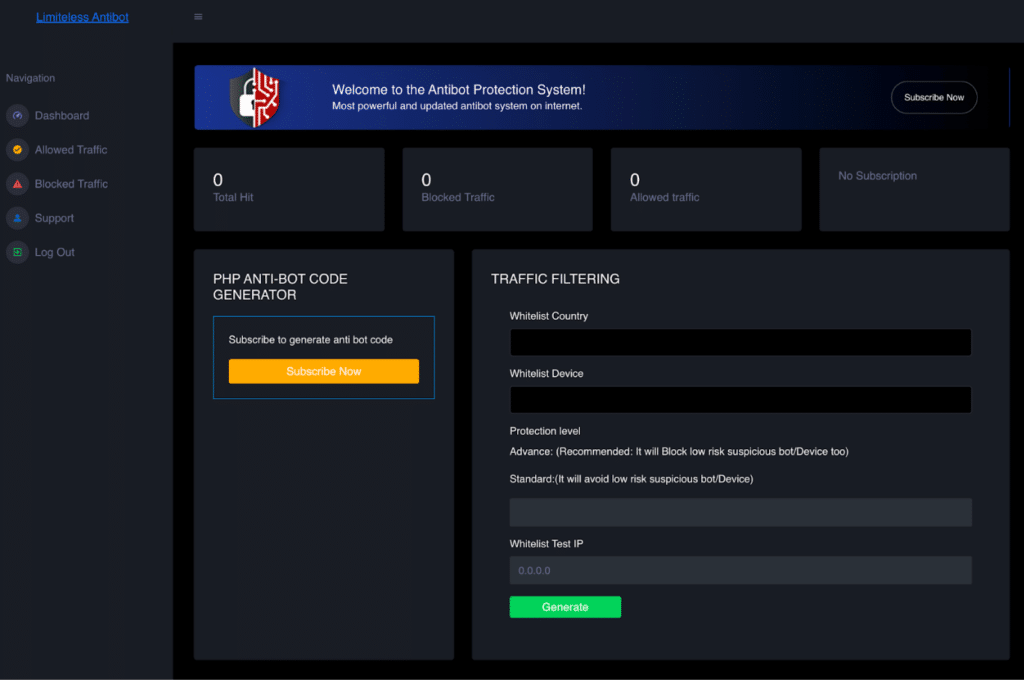
The cybercrime forum thread design for Limitless Anti-Bot
Limitless offers two levels of protection: the standard level, which avoids blocking low-risk bots and devices, and an advanced level that blocks even slightly suspicious traffic.
For information about the above anti-bot services and how to protect phishing attacks, reach out to a SlashNext rep.
How Anti-Bot Services Work
The inner workings of anti-bot services are based on a combination of several techniques. They are all quite different in some way or another:
Bot Detection and IP Filtering
Most anti-bot services rely on bot detection mechanisms that analyze user-agent strings and IP addresses. Public lists of cybersecurity crawlers are widely available (for example, Shodan), making it easy to filter known security bot traffic. Once an IP address or user-agent is flagged as a security crawler, it is blocked, ensuring the page remains accessible to real users but hidden from cybersecurity entities.
Cloaking Techniques
Anti-bot services often use context-switching or JavaScript (JS) obfuscation to serve different content based on the visitor’s profile. A device’s score (determined through fingerprinting techniques) dictates what content is shown. For example, if a known security crawler attempts to access the page, it might be redirected to benign content, while real users are served phishing content.
Geolocation-Based Targeting
Some campaigns are region-specific, allowing anti-bot systems to block foreign traffic entirely. For example, if a phishing campaign is targeting a Korean bank, the service might allow only Korean traffic to visit the site while blocking foreign IP addresses. This method can even be drilled down to the city level, ensuring the page remains under the radar of international cybersecurity services.
CAPTCHA and Challenges
By introducing CAPTCHA or challenge pages, anti-bot services can filter out automated scanners that would normally analyze a web page for malicious content. Since most bots cannot solve CAPTCHAs, this technique effectively blocks them while allowing real users through. Moreover, some systems might introduce a time delay, further confusing security bots by making them “time out” before they can scan the page.
Do Anti-Bots Really Work?
The short answer is: yes, they do, but with limitations. In the less sophisticated end of phishing campaigns, these services work well because many security vendors openly declare their bots and crawlers in the user-agent string. For example:
Palo Alto (note the user agent)
172.71.6.74 – – [12/Oct/2024:08:13:18 +0100] “GET / HTTP/1.1” 200 1926 “-” “Expanse, a Palo Alto Networks company, searches across the global IPv4 space multiple times per day to identify customers’ presences on the Internet. If you would like to be excluded from our scans, please send IP addresses/domains to: [email protected]”
PC Risk (note the user agent)
162.158.94.108 – – [12/Oct/2024:12:15:28 +0100] “GET /cookie-policy HTTP/1.1” 200 7174 “http://google.com” “Googlebot”
Malcure (note the user agent)
172.71.159.72 – – [12/Oct/2024:12:22:15 +0100] “GET / HTTP/1.1” 200 1922 “https://www.google.com/images/url” “Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)”
VirusTotal (note the user agent)
172.68.245.113 – – [12/Oct/2024:12:27:47 +0100] “GET /favicon.ico HTTP/1.1” 200 296 “https://slashnext.com/” “Mozilla/5.0 (X11; Ubuntu; Linux i686 on x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2820.59 Safari/537.36 VirusTotalBot”
It’s relatively easy to identify and block known crawlers by their user-agent strings. This allows cybercriminals to filter out bot traffic, prolonging the lifespan of phishing campaigns. However, in more sophisticated phishing operations, manual analysis by analysts will eventually detect the page, leading to its inclusion on blocklists.
Defeat Phishing With SlashNext
To combat the growing threat of anti-bot technology, SlashNext offers a comprehensive solution. SlashNext Complete™ is an integrated cloud messaging security platform that detects threats in real-time across email, mobile, and web messaging apps with 99.99% accuracy.
SlashNext protects organizations from data theft and financial fraud breaches by providing integrated cloud messaging security for email, browser, and mobile. Our approach helps defend against the latest phishing tactics, including those leveraging advanced techniques.
Get protected and learn more about SlashNext Complete™.