Key Findings
- 7.8 million compromised user records found on the Dark Web
- 57% of exchanges are targeted by at least 1 ongoing phishing campaign
- 74% of web applications contained outdated software, libraries or frameworks
- 25% of web applications contained publicly known web security vulnerabilities
- 67% of web applications failed GDPR compliance, 58% failed PCI DSS compliance
- 32% of web servers had insecure or obsolete encryption protocols in their TLS stack
- 24% of mobile apps contained at least one high-risk mobile security vulnerability
- 1 in 5 mobile apps sends or receives some data using a plaintext HTTP protocol
- 1 in 3 web servers has no support whatsoever of Post-Quantum Cryptography
- 9 in 10 web applications had one or several privacy issues or failures
Top 3 most secure cryptocurrency exchanges – that had the least number of findings within the scope and methodology of this research – outperforming the others:
- Coinbase – coinbase.com
- UPbit – upbit.com
- Crypto.com – crypto.com
Please note that while the three above-mentioned exchanges performed better than others within the scope and methodology of this research, ImmuniWeb does not imply or certify that they are fully secure, unbreakable or totally safe.
ImmuniWeb has no affiliation or conflict of interest with any cryptocurrency exchange from this research. This research does not provide financial, investment or legal advice.
Table of Contents
1. Introduction
According to Forbes, the global cryptocurrency market cap is over 4 trillion USD and is growing. In early October 2025, the price of Bitcoin, Ethereum, Solana and other popular cryptocurrencies surged to almost all-time record. In the meantime, last year at least 40.1 billion USD were moved to ledger addresses that are known to be connected to illicit activities according to a recent Chainalysis report.
The alarming trend is confirmed by statistics from Kroll, saying that 1.93 billion USD have been stolen in crypto-related cybercrimes in the first six months of 2025 alone, surpassing the total amount stolen in the whole of 2024 according to Kroll’s Cyber Threat Intelligence team.
This research explores the current state of web and mobile application security of the largest cryptocurrency exchanges around the globe. In the past, numerous cases have shown how application security failures led to data breaches impacting cryptocurrency and DeFi companies, resulting in stolen funds, as well as long-lasting negative consequences both for the breached entities and their clients.
It is important to highlight that the mere presence of application security vulnerabilities, misconfigurations or weaknesses in web or mobile apps do not mean or imply that client funds or crypto assets are at risk. Likewise, compromised user credentials available on the Dark Web do not necessarily grant cybercriminals with an access to crypto wallets or custodial funds belonging to the victims.
The ultimate purpose of this research is to review the overall state of application security in the crypto industry in 2025, and to provide concise recommendations on what could be improved to enhance existing application security programs of cryptocurrency exchanges and other businesses active in crypto.
2. Methodology
For the purpose of this research, we used a global ranking of the Top Cryptocurrency Spot Exchanges by CoinMarketCap, containing the 254 largest cryptocurrency exchanges.
For each entity, we tested its primary website, most relevant subdomains that handle or process some user-related or user-submitted data, and mobile apps (where available). In total, we tested 2,138 web applications and 146 mobile applications.
Our free online tools from the ImmuniWeb® Community Edition were used for testing. The tools can be freely leveraged by anyone to replicate the testing results, conduct re-testing or test other resources:
- Website Security Test
- Website Privacy Test
- SSL Security Test
- Mobile App Security Test
- Dark Web Exposure Test
All of the above-mentioned security tests are non-intrusive by their technical nature, meaning that some vulnerabilities or weaknesses that require intrusive testing to be detected could be missed and are thus not covered in this research.
3. Web Application Security
The current state of web application security in the cryptocurrency industry leaves significant room for improvement.
While the main websites of cryptocurrency exchanges were generally found to be well-secured, numerous subdomains, that also handle sensitive or regulated information, contained high- and even critical-risk security flaws that were easily detectable without using intrusive or advanced web security testing techniques.
This situation is likely caused by several factors: increasing pressure on software developers to continually deploy new features and functionalities amid the fierce competition on the global market; the growing use of GenAI to automate coding without adequate security guardrails or proper human oversight; insufficient application security budgets; and the lack of a holistic, enterprise-wide and long-term application security strategy based on risk assessment.
Below is an overall distribution of security grades of tested web applications:
- A: 56.8%
- B: 11.2%
- C: 31.7%
- F: 0.3%
Interestingly, a WAF, or another web security defense mechanism, was missing on as many as 45.1% of tested web applications. While, almost 76.3% of the web applications that had a WAF, also had a built-in defense mechanism against data-scraping bots described in our previous research.
24.9% of tested websites contained outdated web software or components with publicly known security vulnerabilities some of which have been disclosed over 5 years ago:
| Web Security Issue | Percentage |
|---|---|
| Outdated web components, libraries or frameworks | 73.8% |
| Vulnerable web components, libraries or frameworks | 24.5% |
| Outdated Content Management System (CMS) | 1.8% |
| Vulnerable Content Management System (CMS) | 0.4% |
Table 1: Percentage of web applications with web security issues
Because of the vulnerable or outdated software, as well as other weaknesses or misconfigurations, as many as 66.8% of tested websites are not compliant with the data protection provisions of GDPR, while 58.2% of tested websites are not compliant with PCI DSS web application security requirements.
While not all cryptocurrency exchanges are legally required to comply with GDPR or PCI DSS depending on their location, business model and other relevant factors, the non-conformity may indicate an urgent need for improvement.
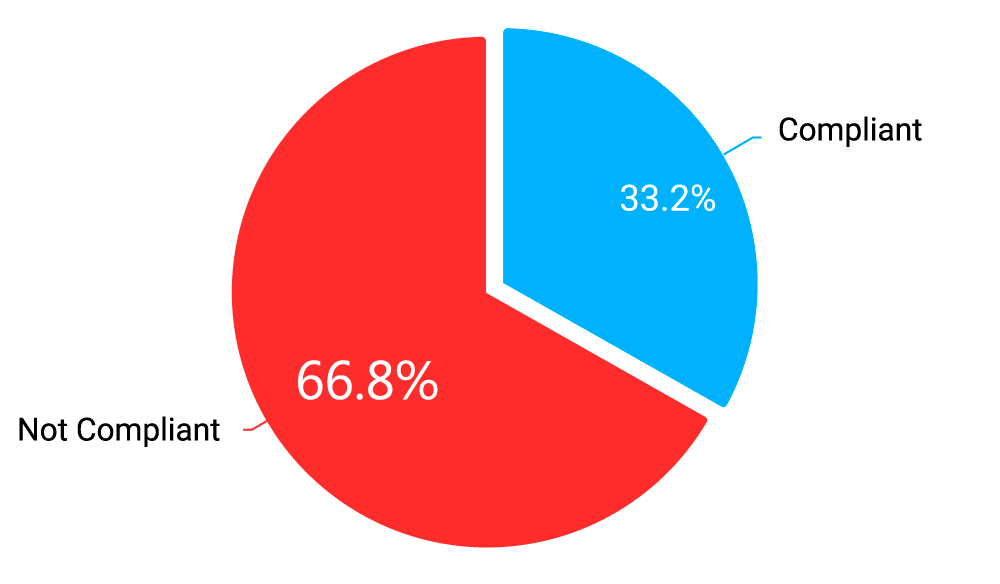
Diagram 1: Websites GDPR Compliance
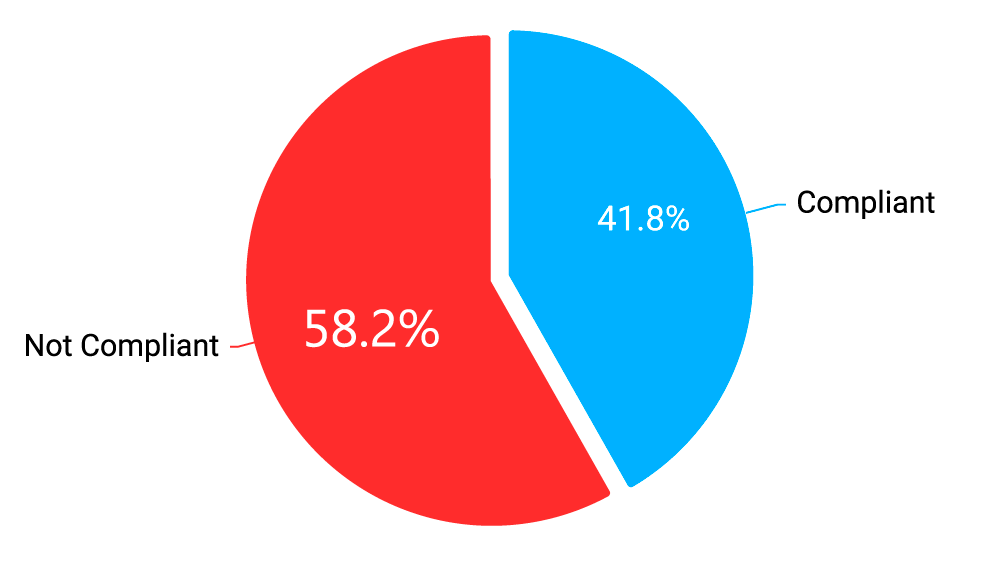
Diagram 2: Websites PCI DSS Compliance
4. Website Privacy Protection
Privacy protection is often a crucial factor for clients when choosing cryptocurrency exchanges. Unfortunately, our research reveals that most exchanges do not yet take user privacy seriously enough, with 9 in 10 web applications being prone to various privacy issues or failures.
This may be caused by the rapidly evolving privacy legislation around the globe, overregulation and overall compliance fatigue, as well as different business priorities that crypto companies have amid the global economic turbulence. It is, however, essential to remember that in many jurisdictions, non-compliance with enacted privacy laws or regulations may lead to hefty monetary fines, revocation of business licenses and other regulatory penalties.
Below is an overall distribution of privacy grades of tested web applications:
- A: 52.4%
- B: 28.3%
- C: 8.2%
- F: 11.1%
The vast majority (89%) of tested web applications has one or several privacy issues including:
| Website Privacy Issue | Percentage |
|---|---|
| Privacy policy not found on the website | 40.4% |
| Cookie consent banner is missing while third-party cookies are set | 37.1% |
| Cookie consent banner is missing | 45% |
| Tracking pixels are used | 15.3% |
Table 2: Percentage of web applications with privacy issues
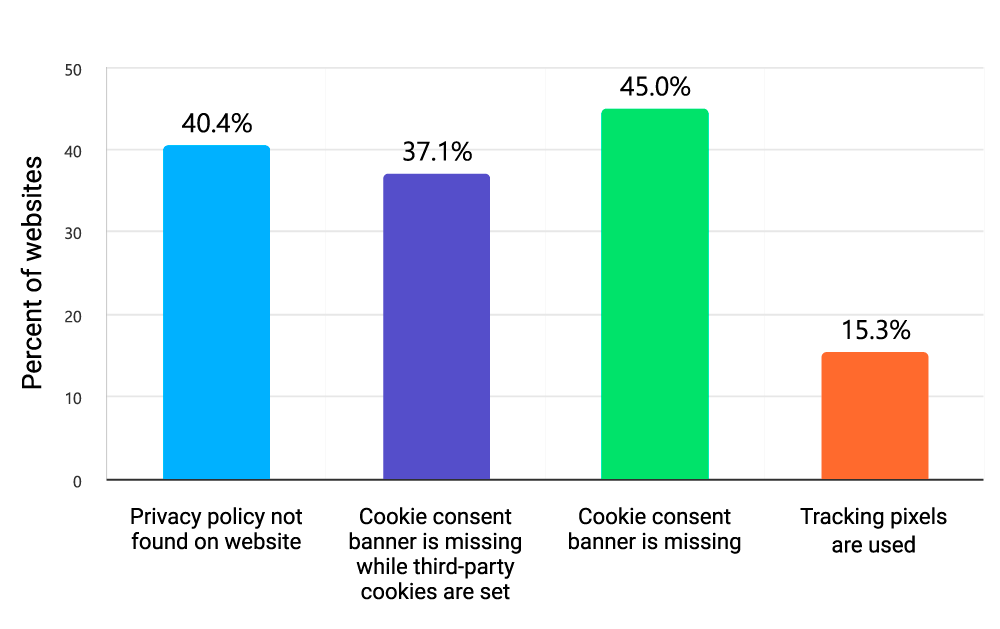
Diagram 3: Websites Privacy Issues
5. SSL/TLS Encryption and Security
Properly implemented HTTPS encryption has been a foundational requirement of robust application security, designed to prevent interception and theft of sensitive user data in transit between web browser and remote web server. It may also serve as a litmus test when assessing the overall maturity of application security program of a company.
Most organizations that still have obsolete encryption protocols, such as TLS version 1.0, probably have serious challenges with both shadow IT and configuration management of their IT systems. This may be caused by migration to cloud environments without a comprehensive plan on to how to discontinue their on-premise IT assets; third-party hosted systems without adequate inventory, monitoring and supervision; lack of time and ongoing stress of cybersecurity teams that are outnumbered by cybercriminals; and the abundance of more urgent tasks and security incidents that push cybersecurity teams to continually postpone everything that is not an emergency.
Below is an overall distribution of security grades for SSL/TLS stack of tested web servers:
- A: 77.9%
- B: 17.8%
- C: 2.1%
- F: 2.2%
While the majority of web servers performed reasonably well overall, their readiness for Post-Quantum Cryptography (PQC) – testable with the new PQC-specific check recently added to our SSL test – was missing on 1 in 3 web servers.
While the full support of ML-KEM (Module-Lattice-Based Key-Encapsulation Mechanism Standard by NIST) is not yet expected from organizations to be deployed in production, it zero adoption may possibly be an alarming signal indicating that full migration will be a long and painful exercise:
| PQC Support in TLS | Percentage |
|---|---|
| No support of hybrid ML-KEM algorithms | 29.7% |
| No support of ML-KEM post-quantum algorithms | 100% |
Table 3: Percentage of web servers lacking PQC support
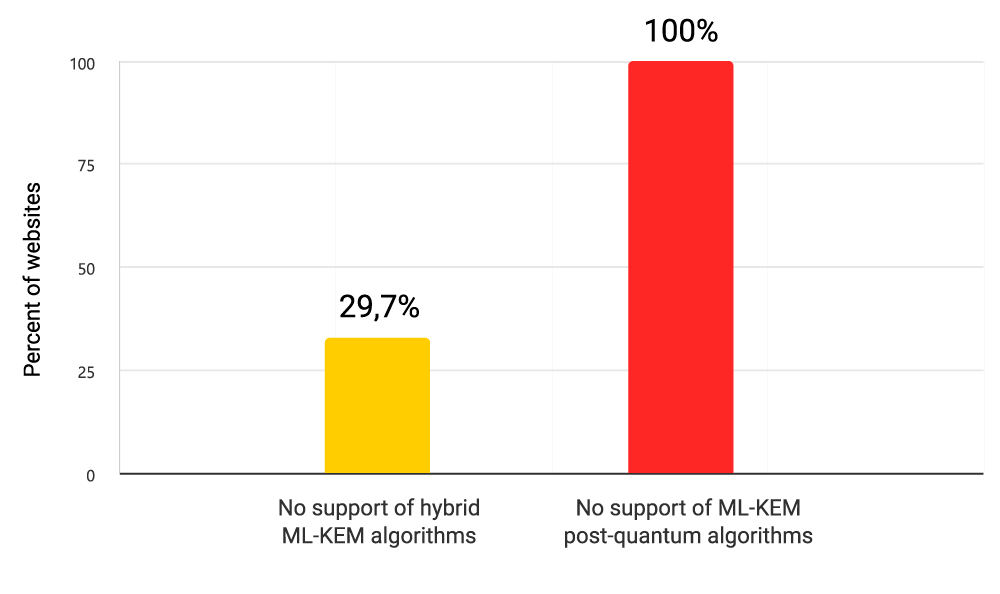
Diagram 4: Post-Quantum Cryptography (PQC) Support in TLS
Moreover, 31.7% of web servers still support one or several obsolete, deprecated or insecure encryption protocols:
| HTTPS Security Issue | Percentage |
|---|---|
| TLS version 1.0 enabled | 15.4% |
| TLS version 1.1 enabled | 18.5% |
| No TLS/SSL encryption at all | 1.2% |
| No redirect from HTTP to HTTPS | 15.8% |
Table 4: Percentage of web servers with weak encryption
Compliance with industry standards that require proper configuration of HTTPS encryption is also tellingly low: 65.1% of tested web servers fail PCI DSS requirements related to TLS configuration, while 98.8% fail NIST compliance (NIST SP 800-52) due to comparatively strict encryption requirements imposed by NIST.
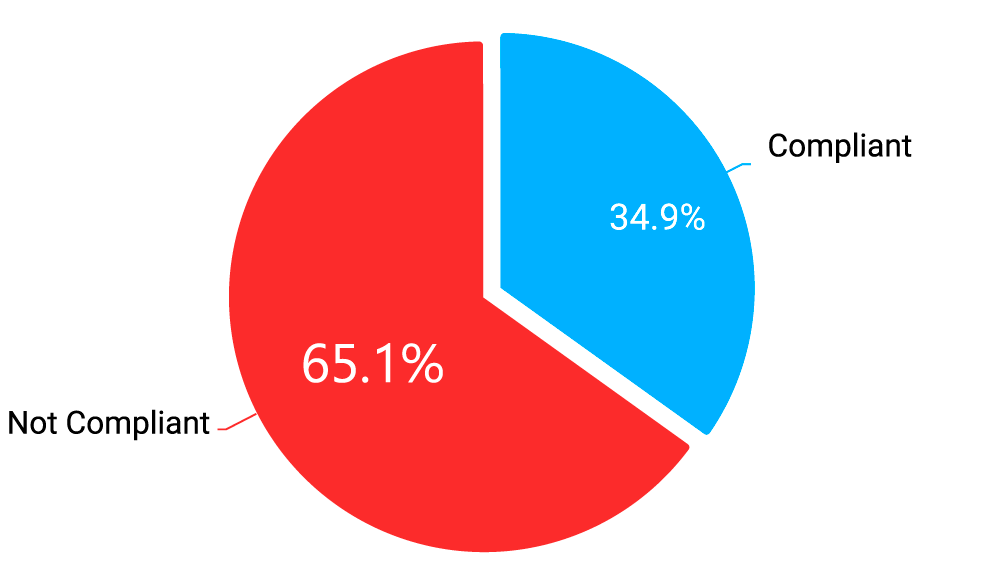
Diagram 5: Web Servers PCI DSS Compliance
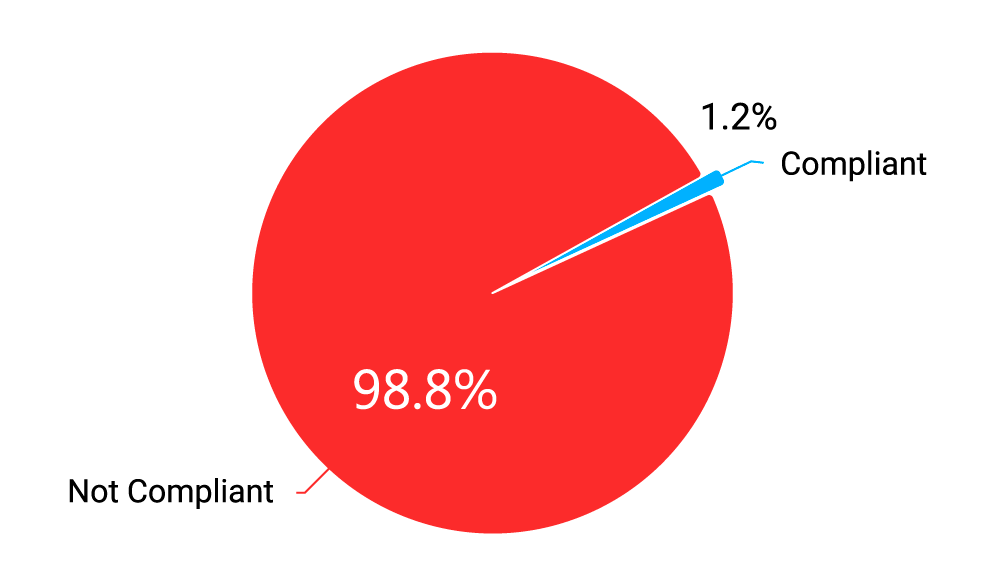
Diagram 6: Web Servers NIST Compliance
6. Mobile Application Security
Many cryptocurrency exchanges in this research have a mobile app, while some maintain several mobile apps. Not all mobile apps allow users to control their funds or perform other sensitive operations, but compromise of a mobile app will likely provide attackers with a significant advantage to continue their attack to eventually misappropriate crypto funds or cause other serious damage.
Most mobile apps from this research contained various security and privacy related issues, some of which are fundamental and could have been found with an automated vulnerability scanner. The root cause of this problem is likely similar to the web application security issues: growing pressure on software engineers to deliver more in a shorter timeframe; ad hoc use of GenAI to accelerate coding without human supervision or control; and the lack of a company wide application security program that would assign clear roles and responsibilities, while enabling and empowering people to perform them.
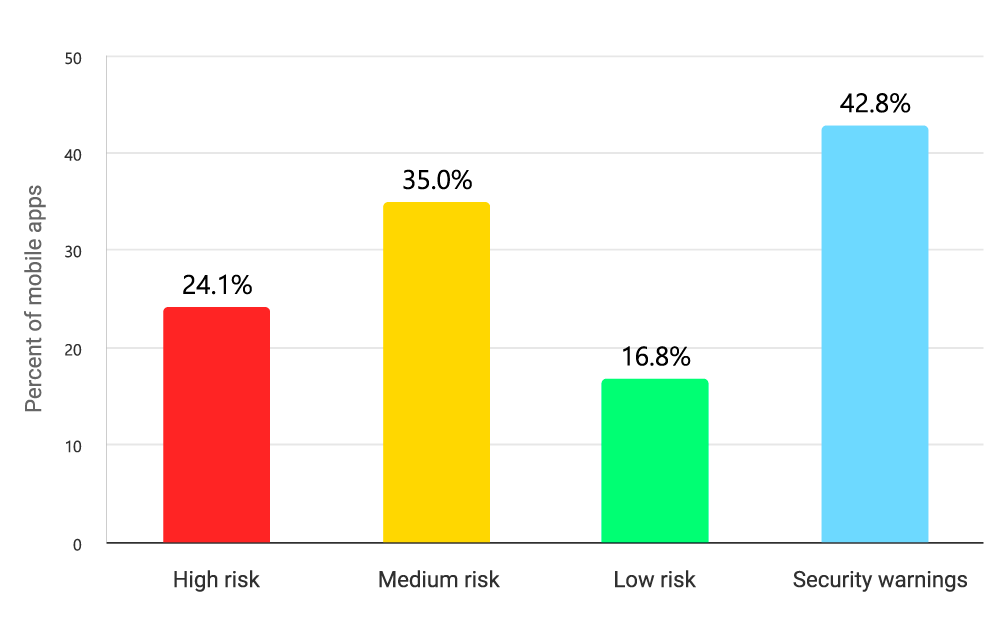
Among the 146 mobile apps from the tested cryptocurrency exchanges, 24.1% contained high-risk vulnerabilities detected by SAST or DAST scans of the application binary, as well as other lower-risk vulnerabilities, in total 3,785 mobile security issues were found:
| Mobile App Vulnerabilities | Percentage |
|---|---|
| High Risk | 24.1% |
| Medium Risk | 35% |
| Low Risk | 16.8% |
| Security Warnings | 42.8% |
Table 5: Percentage of mobile apps containing security issues
Last, as many as 28 out of 146 mobile apps (19.2%) contained web calls to external APIs or microservices to transfer some data without using TLS encryption at all, relying on a cleartext HTTP protocol.
7. Dark Web Exposure
The vast number of stolen credentials and other sensitive data circulating on the Dark Web is a well-known threat that affects nearly every industry and sector of the modern economy.
However, cryptocurrency exchanges are expected to uphold higher security standards than most other sectors, given the sensitive and high-value nature of operations, as well as higher profit margins compared to many other businesses. Yet several factors continue to contribute to data leaks and breaches, which eventually expose sensitive data on the Dark Web. These include nascent or even absent third-party risk management programs (TPRM) when data theft occurs via insecure vendors or suppliers; insufficient budgets allocated to incident detection and response that could potentially contain a breach before the data is exfiltrated; and excessive workload of cybersecurity analysts and incident responders up to burnouts.
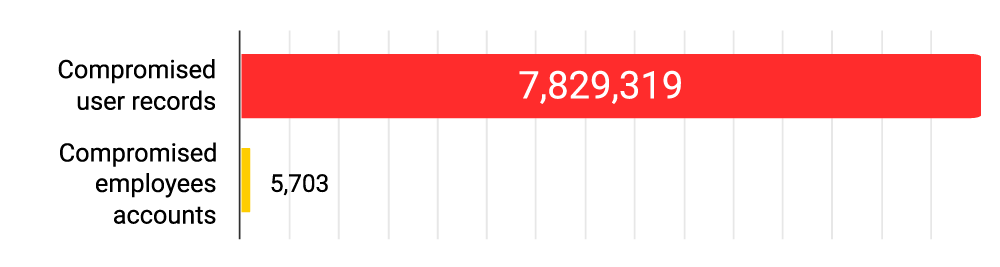
In total, at least 7,829,319 compromised user records (e.g. various records of clients, leads or partners of cryptocurrency exchanges) from tested cryptocurrency exchanges were found on the Dark Web. Over 30% of the records contain sensitive personal data or passwords in plaintext. Sources of the data breaches include attacks of ransomware groups; compromise of cryptocurrency exchanges’ web applications or other IT systems by various cyber-threat actors including hacktivists and state-sponsored actors; and third-party incidents, such as compromise of an exchange’s vendors or suppliers.
46% of the tested cryptocurrency exchanges have their own employees’ credentials present in various Dark Web leaks, containing at least 5,703 unique employees accounts.
8. Phishing and Domain Squatting
The majority of cryptocurrency exchanges in this research experience ongoing phishing and impersonation campaigns, which target either their employees or clients. The situation is not uncommon because of the high costs required to prevent such attacks, while the growing erosion of international legal cooperation creates safe harbors in some jurisdictions for cybercrime groups that may host illicit and fraudulent content in impunity.
Nonetheless, given that phishing and impersonation attacks may cause significant financial losses to clients of cryptocurrency exchanges, the latter should consider enhancing their monitoring, detection and shutdown capacities to quickly neutralize malicious websites, domains and fake accounts in social networks. Ongoing user awareness campaigns about the cyber threats may also help to reduce the eventual impact of phishing and scam campaigns.
Below are telling numbers about the current number of phishing and related fraud campaigns currently deployed against the cryptocurrency exchanges from this research, with at least:
- 56.8% of tested cryptocurrency exchanges have at least 1 ongoing and currently active phishing campaign with 453 phishing campaigns in total.
- 79.6% of tested cryptocurrency exchanges have at least 1 ongoing and currently active cyber-squatting domain with 6,314 cyber-squatting domains in total.
- 76.4% of tested cryptocurrency exchanges have at least 1 ongoing and currently active typo-squatting domain with 1,614 typo-squatting domains in total.
- 14% of tested cryptocurrency exchanges have at least 1 ongoing and currently active fake accounts in social media with 4,994 fake or impersonating accounts in social media.
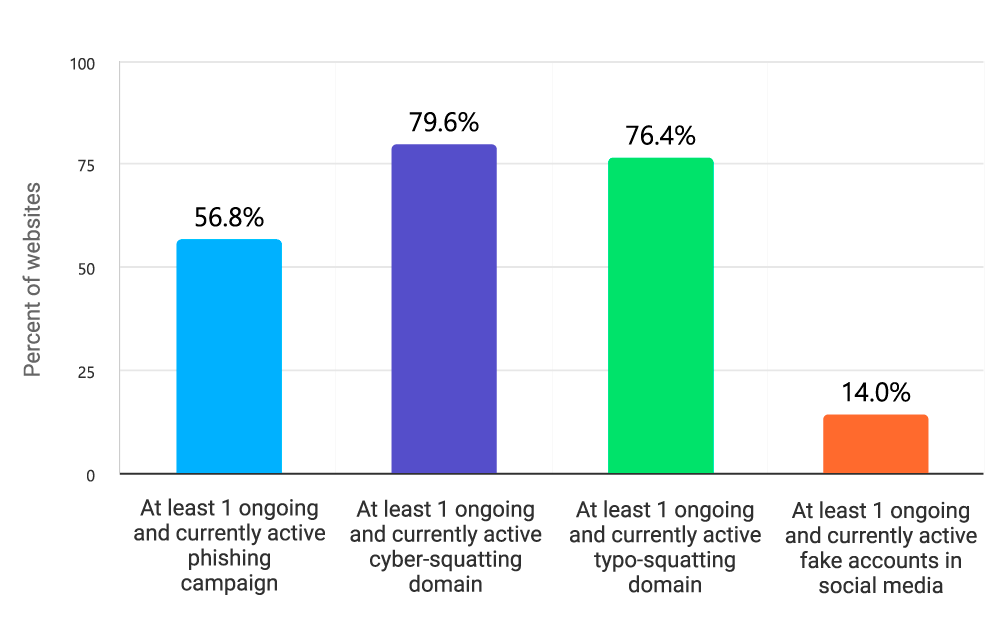
Diagram 9: Phishing and Domain Squatting
9. Conclusion
Dr. Ilia Kolochenko, Chief Architect & CEO at ImmuniWeb, says: “This research is a good reminder that no industry is immune from cybersecurity or data protection risks and challenges. Having said this, the crypto sector has a strategic advantage over, for example, traditional banking industry. Majority of its players are recently founded companies that are not encumbered by legacy IT systems, which most other financials organizations have to maintain and protect. Many other sectors of economy struggle to reconcile their obsolete IT systems, developed in late 90s but still used in production environment, with complex multicloud environment, container orchestration, LLMs, IoT and other new technologies chaotically deployed around the globe. Many crypto organizations have had a chance to build their networks from scratch relying on modern-day technologies.
Given that security incidents and data breaches may cause substantial damage to clients of crypto businesses, it is essential that the latter reconsider their investment priorities and pay more attention to their cybersecurity programs. Of note, spending more does not necessarily mean spending wiser. It is crucial to have a cybersecurity strategy based on a comprehensive risk assessment, bringing cybersecurity, legal and business professionals to the table to ensure a holistic and multidisciplinary approach to corporate cybersecurity governance. Otherwise, a company may triple its current cybersecurity budget but will still fall victim to a data breach. Likewise, continuous investment in employee education is crucial, otherwise, even the cutting-edge cyber defense mechanisms will bring little to no value.
Finally, organizations shall bear in mind that mere compliance with a specific cybersecurity standard or framework is not a ceiling but a floor of their data protection strategy. It is, therefore, essential to ensure that your data is truly safe, even if some security controls or procedures are not expressly imposed by applicable law. We sincerely hope the crypto industry will embrace these simple principles and become a North Star for corporate data protection across the broader economy.”
Below are possible actions that cryptocurrency exchanges and other companies in crypto industry may consider to implement in order to improve their current state of application security:
- Implement a holistic, enterprise-wide and long-term application security strategy
- Shift to security-by-design and privacy-by-default principles for software development
- Create, enforce and continually improve a policy on the use of GenAI for software development
- Ensure that security and privacy are embedded since day one of application development cycle
- Design, implement and continually improve risk-based third-party risk management program
- Perform continuous monitoring of attack surface including cloud and third-party assets
- Monitor and respond faster to phishing, scam and impersonation campaigns
- Invest more in both employee and client security training and awareness
- Create dedicated roles of CISO and Data Protection Officer (DPO)
Use and distribution: you are welcome to utilize the above-mentioned content for non-commercial purposes if you make a clear attribution to ImmuniWeb, with a backlink to this page when practical. In case of doubt, please contact us.